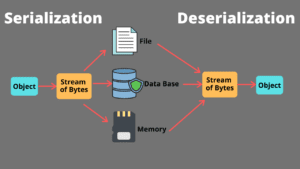
What is Serialization?
Serialization is the process of converting an object in memory into a format that can be stored or transmitted. This format is often a sequence of bytes. It allows objects to be persisted across different contexts or transferred over networks.
What is Deserialization?
Deserialization is the reverse process of Serialization. It takes a serialized representation of an object and reconstructs it in memory. This is done to restore the object’s state and functionality.
What is Insecure Deserialization?
Insecure deserialization occurs when an application deserializes untrusted or tampered data without proper verification, allowing attackers to manipulate the serialized object. Serialization is the process of converting an object into a format (like JSON or XML) that can be stored or transmitted, while deserialization is the reverse. When deserialization is done insecurely, it can lead to code execution, privilege escalation, or other harmful behaviors.
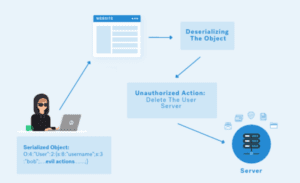
How Do Insecure Deserialization Attacks Arise?
These attacks arise when user input is deserialized without adequate validation. Common reasons include:
- Lack of Input Validation: Applications often trust serialized objects received from users, assuming they are safe.
- Use of Unsafe Libraries: Some Serialization frameworks lack security features to validate objects, making them vulnerable.
- Data Manipulation Possibilities: Attackers can tamper with the serialized data to include malicious payloads, which will execute upon deserialization.
What is the Impact of Insecure Deserialization Attacks?
- Remote Code Execution (RCE): An attacker could gain the ability to execute arbitrary code on the server.
- Privilege Escalation: Malicious users may elevate their privileges and gain unauthorized access to sensitive information.
- Denial of Service (DoS): Attacks could crash the application or exhaust server resources, making the service unavailable.
- Data Manipulation: Attackers can modify application state, which might lead to data breaches or corrupted data.
How to Exploit Insecure Deserialization Attacks?
- Identify Vulnerable Deserialization Functions: An attacker identifies deserialization functions in the application that receive user-supplied data.
- Create a Malicious Payload: The attacker modifies the serialized data to inject a payload, often leveraging libraries or tools like ysoserial to craft serialized objects that can execute commands.
- Send the Malicious Object: The malicious serialized object is sent to the vulnerable endpoint. If deserialized without validation, the payload will be executed on the server.
- Gain Access: Depending on the application’s logic and the attacker’s objective, they can perform a variety of attacks, such as executing shell commands, reading files, or modifying data.
How to Prevent Insecure Deserialization Attacks?
- Avoid Serialization of Sensitive Data: If possible, avoid serializing user-controllable data. Limit serialization to data not controlled by external sources.
- Implement Data Integrity Checks: Use digital signatures or hashing to verify the integrity of serialized objects before deserialization. This ensures they haven’t been tampered with.
- Use a Safe Deserialization Method: Consider using safer data formats like JSON, which limit the complexity of serialized data, or use serialization libraries that support whitelisting classes allowed for deserialization.
- Restrict Object Types During Deserialization: Ensure that only expected object types are allowed during the deserialization process, to prevent unexpected object creation.
- Implement Application-Level Monitoring: Set up monitoring to detect unusual behavior that may indicate exploitation attempts, such as attempts to deserialize unexpected data structures or types.
Thank you for taking the time to explore Insecure Deserialization Attacks with us. Understanding how these vulnerabilities work and the risks they pose is key to keeping your applications secure and resilient.
In our next blog, we’ll dive into another interesting vulnerability, continuing our journey into the world of cybersecurity.
Stay tuned, and let’s keep building stronger defenses together!



