Operational Technology Penetration Testing, or OT pen testing, is a specialist security evaluation procedure that concentrates on finding weaknesses in Supervisory Control and Data Acquisition (SCADA) and Industrial Control Systems (ICS) systems. These systems are essential for keeping an eye on and managing physical operations in key infrastructure sectors, such as:
- Production and distribution of power
- Production (plants, refineries)
- Transportation (railroads, air traffic control)
- Distribution and treatment of water
- pipes for gas and oil
Goals of OT Pentesting?
The primary goal of OT (Operational Technology) penetration testing is to proactively identify weaknesses in an OT environment’s security posture before malicious actors can exploit them.
Here’s a breakdown of what OT pen-testing aims to achieve:
-
Vulnerability Identification:
Uncover security holes in software, hardware, network architecture, and configurations used within the OT system. This helps prioritize patching and remediation efforts.
-
Security Control Assessment:
Evaluate the effectiveness of security controls like firewalls and access controls.
-
Attack Simulation:
Simulate real-world attack scenarios to understand potential attack vectors and the impact they could have on operations. This helps improve incident response preparedness.
-
Improved Security Posture:
By identifying vulnerabilities and controlling weaknesses, OT pen testing provides valuable insights for strengthening the overall security posture of the OT environment.
What is the difference between IT pen-testing and OT pen-testing?
| Key point | IT Pentesting | OT Pentesting |
| Focus | Primarily focuses on the security of information technology (IT) systems, including servers, databases, applications, networks, and user devices. The goal is to identify vulnerabilities that could allow attackers to steal, manipulate, or disrupt sensitive data. | Targets the security of operational technology (OT) systems, which control and monitor physical processes in critical infrastructure sectors like power generation, manufacturing, transportation, and water treatment. The objective is to find weaknesses that could allow attackers to disrupt or manipulate physical operations, potentially causing safety hazards and financial losses. |
| Risk and Impact | The main concerns are data breaches, unauthorized access, and information disclosure. While these can be financially damaging, the impact tends to be more indirect. | Deals with potentially higher risks due to the connection between cyberspace and the physical world. Successful attacks could lead to equipment damage, production outages, safety incidents, and environmental damage. |
| Systems and Technologies | Primarily deals with traditional IT technologies like operating systems, databases, web applications, and network devices. Testers rely on tools and techniques designed for these environments. | Often involves specialized industrial control systems (ICS) and SCADA (Supervisory Control and Data Acquisition) systems. Testers require expertise in these specific technologies and their unique vulnerabilities. |
| Regulations and Compliance | It is subject to general data protection regulations and industry standards, depending on the type of data involved. | Often, they need to adhere to stricter regulations specific to critical infrastructure sectors (e.g., NERC CIP in North America) to ensure safety and operational integrity. |
| Testing Approach | It involves more aggressive techniques to simulate real-world attack scenarios, potentially disrupting normal operations temporarily. | It usually requires a more cautious approach due to the potential consequences of disrupting critical processes. Testers might prioritize non-invasive methods and focus on identifying vulnerabilities for later remediation. |
| Skills and Expertise | Focuses on general IT security knowledge and proficiency in standard testing tools. | It often demands additional expertise in ICS/SCADA systems, industrial protocols like Modbus and DNP3, and a deeper understanding of physical processes to assess the potential impact of vulnerabilities. |
| Collaboration | Collaboration primarily occurs between security professionals and IT teams. | It often requires collaboration between security professionals, OT engineers, and process control experts to understand the potential risks and ensure safe testing procedures. |
Why is OT testing required?
-
Aggressive Threat Identification:
OT pen testing takes a proactive stance in contrast to reactive actions performed following a security compromise. It assists in locating weak points in your OT systems before hackers may take advantage of them. This becomes particularly crucial as these systems become more digitalized and networked, which increases their vulnerability to hackers.
-
Decreased Chance of Successful Incidents:
OT pen testing helps you find security flaws early on, so you can fix them before an attack is successful. By doing this, the likelihood of operational disruptions, possible safety risks, and data breaches is greatly decreased.
-
Respect for regulations:
A lot of sectors have laws in place requiring particular security procedures for OT systems. By proving that you’ve taken action to find and fix potential security vulnerabilities, OT pen testing helps make sure you abide by these rules.
-
Enhanced Security Attitude:
OT pen-testing is more than just finding security holes. It offers a thorough evaluation of your OT security posture and points out any shortcomings. This gives you the ability to strengthen your defense against cyber threats by putting in place the appropriate precautions and countermeasures.
-
Increasing Stakeholder Trust:
Consistent OT pen-testing shows a dedication to cybersecurity, which can increase stakeholder trust among partners, consumers, and investors. For businesses whose primary functions significantly depend on operational technology, this is especially crucial.
What are the benefits of OT pen-testing?
The breadth and complexity of this service are customized to meet your unique requirements. Typical evaluations that are done are:
![]()
![]()
![]()
- An internal attacker may penetrate or harm the network, systems, or data by using an internal penetration test, which mimics an insider threat.
- The purpose of an external penetration test is to identify and take advantage of security holes in hosts that are reachable through networks outside of the operating system (OT) (e.g., IT, the Internet).
- The application penetration test mimics system attacks to obtain unauthorized access.
- Find weak points in your wireless network setup with a wireless penetration test.
- A formalized report that includes the following is used to document the outcomes of the evaluation activities:
- Methodology for assessment; executive overview; comprehensive technical analysis; and recommendations for correction.
- identified security flaws that have been categorized based on their likelihood of occurrence and their effect.
Market Analysis of OT Pentesting:
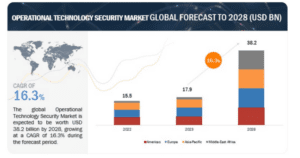
The global OT security market is expected to grow from an estimated value of USD 17.9 billion in 2023 to 38.2 billion USD by 2028, at a compound annual growth rate (CAGR) of 16.3% from 2023 to 2028. This growth is expected to occur at a compound annual growth rate (CAGR) of 16.3% from 2023 to 2028. The OT security market presents a lucrative opportunity for technology vendors and is anticipated to experience significant expansion over the next five years.
We base all of our OT penetration tests on industry best practices as established by the following guidelines:
- NIST SP 800-82: Guide to Industrial Control Systems (ICS) Security
- ISA/IEC 62443: Cybersecurity for Industrial Automation and Control Systems
- NIST Cybersecurity Framework (CSF)
- ISO/IEC 27001: Information security management systems
- OWASP Top 10 for ICS Security
- SANS Institute: Top 20 Critical Security Controls for Effective Cyber Defense
- ENISA (European Union Agency for Cybersecurity) Good Practices for Industrial Control Systems Security CIS Controls for OT Security
- FERC (Federal Energy Regulatory Commission) Cyber Security and Physical Security Standards.
Conclusion:
One of the most important procedures for protecting vital infrastructure systems is operational technology (OT) penetration testing. Strong security measures are becoming important as sectors including manufacturing, transportation, water treatment, and power generation digital and network their processes more. OT pen testing is a proactive approach that finds and fixes vulnerabilities before bad actors can take advantage of them.
To sum up, every firm that relies on industrial control systems must prioritize OT pen testing as a strategic need in addition to a technical one. In order to maintain the safe and effective functioning of vital infrastructure in a world that is becoming more interconnected, it offers a thorough assessment of security vulnerabilities as well as practical ideas to strengthen defenses.



