What is a container?
An isolated environment known as a container allows an application to operate without influencing other parts of the system or the application affecting the system. Containers are ideal for safely executing software such as databases or web applications that require access to sensitive resources but do not want to grant all users on the system access because of their isolation.
The container is lightweight compared to other executables since it runs natively on Linux and shares the host machine’s kernel. A container won’t restart itself after it stops unless you specifically configure it to. Nonetheless, since they do not require the overhead of a whole operating system, containers have the potential to be far more efficient than virtual machines. They boot in seconds rather than minutes and share a single kernel with other containers.
Applications can be packaged with all the parts they require in containers and then shipped as a single unit. Because it reduces friction between the development, QA, and production environments, this method is well-liked because it allows teams to release software more quickly.
When developing with other developers, “it works on my machine” issues are eliminated when building and deploying apps within software containers. Containers guarantee consistency across different computing environments, so users may be confident that their application will function consistently wherever it is installed.
Additionally, Docker containers can operate in any cloud and on any infrastructure. You have more control and security when you can isolate individual apps from other apps and the infrastructure that supports them.
Why is container testing required?
With the increasing popularity of container-based applications, the subject of how to improve container security becomes inescapable. Hackers are increasingly attempting to attack hosts and run malicious containers using unpatched vulnerabilities in Docker images. Fortunately, penetration testing (pen testing) helps defend your containerized systems from these assaults.
Businesses frequently choose to containerize systems to accelerate development and release. However, StackRox says that over half of enterprises admit to delaying the deployment of container-based apps owing to security concerns.
According to StackRox’s analysis, the majority of firms had a container-related security issue in the previous year. The most prevalent security concerns encountered by businesses include data exposure as a result of container and Kubernetes misconfiguration, significant container vulnerabilities, runtime threats, and IT compliance failures.
Docker container security is crucial given the role containers play in modern application creation and implementation. Containers isolate applications and their dependencies, maintaining consistency across environments. However, their broad use makes them an attractive target for perpetrators. Security flaws in containers can result in data compromises, illegal access, and system compromises. Continuous vulnerability assessments, correct setup, and access restrictions are critical for protecting sensitive data, maintaining system integrity, and ensuring compliance with industry standards. The robust security of containers reduces risks and assures the reliability of applications that are containerized.
In this essay, I will describe the significance of pen testing Docker containers and guide what to consider while performing such tests.
Reveal Container Vulnerabilities with Pentesting:
Performing penetration tests is a useful method for ensuring the security of container-based systems. It allows you to examine containers from the attacker’s perspective and identify vulnerabilities at all phases of a container’s life cycle, including development, deployment, and execution.
There are two methods for testing containers:
- Static vulnerability analysis detects known flaws when scanning container images.
- Dynamic vulnerability analysis identifies unusual container behaviour during runtime. This strategy is effective with undiscovered flaws and threats, although it may be constrained by testing tools.
Security experts recommend utilizing dynamic scanning in conjunction with static container analysis to detect malicious container activity. Submitting containers to comprehensive stress tests during pen testing allows you to uncover two of the most frequent security risks: container vulnerabilities and misconfiguration.
Here are five tips for efficient pen testing Docker containers:

- Have a detailed plan for a security audit. We take the Center for Internet Security (CIS) Docker Benchmarksas a starting point for container security testing because CIS provides a step-by-step checklist to secure Docker containers. Nevertheless, before conducting any CIS tests, make sure you have access to the container environment. If you don’t, you’ll only be able to finish the fourth step of the CIS checklist (container images and build file configuration).
- Always scan container images for vulnerabilities. Even if you’re working with container images from reputable sources, you must ensure the security of each picture and its layers. Use the Common Flaws and Exposures record and CVE Details to ensure that installed apps do not include known or unfixed weaknesses.
- Use dependency analysis. You can use this to check the dependency graph of software present in a container image to identify dependencies with known vulnerabilities.
- Perform automated code reviews for applications running in containers. Your choice of automated code review tools will depend on the programming language, components, and architecture you use. For instance, if you’re using Go, you can run Go Vet for automatic analysis. To run a static analysis of Python code, you can use Mypy and SonarLint. To achieve better code coverage, consider combining several code analysis tools. Reduce effort by picking a series of scripts to automate different phases of assessment. You may utilize both bespoke and open-source scripts with additional features. Also, don’t limit your research into testing to automated tests, which might produce a lot of “negative” results.
- Perform manual code reviews. Manually checking your code is required to ensure that automated tests do not provide false positives. For an efficient manual code review, concentrate on the most important parts of your application’s code.
Knowing the intricacies of the programming language is essential for excellent code review. Delegate manual code review exclusively to highly trained testers and engineers.
While containerization is a viable method of software development, it introduces several security problems. Examining your application from the perspective of an attacker can help you identify hidden security flaws and avert catastrophic data breaches.
Always remember to carefully examine your application’s code and do any essential tests on all container images, regardless of how dependable their sources are. Effective audit preparation can help you organize and streamline the whole pen testing process.
These are the top 10 vulnerabilities found in containers.
1. Insecure Container Images
- Image Vulnerabilities: Using container images with known vulnerabilities can expose the entire infrastructure to attacks. Regularly scan container images for vulnerabilities and keep them up-to-date.
2. Misconfigured Container Runtimes
- Inadequate Isolation: Misconfigurations in container runtimes can weaken isolation between containers, allowing unauthorized access and lateral movement. Configure runtimes securely to avoid such risks.
3. Weak or Outdated Container Dependencies
- Outdated Libraries and Frameworks: Containers often include dependencies such as libraries and frameworks. These can contain security vulnerabilities. Regularly update and patch dependencies to mitigate risks.
4. Insecure API Interfaces
- Exposed APIs: Insecurely exposed container APIs open opportunities for unauthorized access and potential exploitation. Properly secure and authenticate API interfaces to prevent unauthorized access.
5. Insider Threats
- Unsecured Access Controls: Weak access controls within containerized environments can facilitate insider threats. Limit and monitor privileged access to containers to mitigate this risk.
6. Data Breaches and Leakage
- Unprotected Secrets and Sensitive Data: Storing sensitive data or secrets within containers without adequate protection can lead to data breaches or unauthorized access. Implement strong encryption and secure storage of sensitive information.
7. Container Breakouts
- Kernel Vulnerabilities and Exploits: Container breakouts exploit vulnerabilities in the underlying host operating system or kernel. Regularly patch and update the host system to mitigate this risk.
8. Insecure Container Registries
- Untrusted Registries: Using untrusted container registries can introduce malicious or tampered images into the environment. Trust only reputable registries and validate the images before deployment.
9. Persistent Storage Risks
- Unsecured Persistent Storage: Data stored persistently within containers should be properly encrypted and protected to prevent unauthorized access or tampering.
10. Lack of Security Monitoring and Logging
- Insufficient Visibility: Failing to monitor and log container activities makes it challenging to identify and respond to security incidents. Implement comprehensive logging and real-time monitoring to detect and mitigate threats.
Best Container Security Tools for 2024

1. Container Image Security
Ensuring the security of your container images is crucial to preventing the deployment of vulnerable or malicious code. The following tools help you scan and validate container images for security risks:
- Grype: A tool for detecting vulnerabilities in container images by analyzing their software dependencies.
- Anchore Engine: A comprehensive container image inspection and vulnerability scanning tool.
- Clair is an open-source tool for the static analysis of vulnerabilities in container images.
- Trivy: A vulnerability scanner specifically designed for containers, providing detailed security reports.
2. Container Orchestration
Container orchestration platforms streamline the deployment and management of containerized applications. The following tools are dominant players in the container orchestration landscape:
- Kubernetes is an industry-leading container orchestration platform used for managing and scaling container deployments.
- Apache Mesos is a highly scalable and fault-tolerant cluster manager capable of handling containerized workloads.
- Nomad: A flexible and easy-to-use container orchestration tool backed by HashiCorp.
3.Runtime Protection
Runtime protection tools operate at the container runtime level to detect and prevent malicious activities and runtime anomalies. The following tools enhance container runtime security:
- Falco: A behavioural activity monitor designed to detect and alert abnormal container behaviour.
- KubeArmor: A Kubernetes-native security solution providing fine-grained container-level security controls.
- Tracee is an open-source runtime security and forensics tool specializing in container threat detection.
- Sysdig is a comprehensive container security platform offering real-time monitoring, threat detection, and forensics capabilities.
4.Vulnerability Management
Effective vulnerability management helps identify and remediate security weaknesses in container deployments. The following tools assist with vulnerability scanning and management:
- Tenable.io: A vulnerability management platform capable of scanning containerized environments.
- Qualys: A cloud-based vulnerability management solution that provides container scanning capabilities.
- Rapid7: A comprehensive security toolset, including vulnerability management for containerized environments.
- DefectDojo is an open-source vulnerability management platform with container security capabilities.
5.Network Security
Securing container networks is crucial to prevent unauthorized access and data breaches. These tools help you implement network security measures:
- Calico is a popular open-source networking solution providing network policy enforcement for container environments.
- Cilium is a powerful networking and security plugin for Kubernetes, providing encryption and fine-grained network policy enforcement.
- Weave Net is a lightweight and easy-to-use container network solution with built-in encryption and network segmentation capabilities.
6. Identity and Access Management (IAM)
Managing identities and controlling access to container environments is critical for maintaining security. These tools facilitate robust identity and access management:
- AWS IAM: The Identity and Access Management service provided by Amazon Web Services for managing access to AWS resources.
- Azure AD is Microsoft Azure’s cloud-based identity and access management solution geared towards securing Azure resources and applications.
- Okta: is a widely used cloud-based IAM platform providing seamless single sign-on and access control capabilities.
- Keycloak: An open-source IAM solution that enables centralized user
7. Incident Response
Efficient incident response tools streamline the detection, notification, and mitigation of security incidents. The following tools enhance incident response capabilities for container environments:
- Demisto: A comprehensive security orchestration, automation, and response (SOAR) platform.
- Splunk Phantom: is a security automation and orchestration platform that helps streamline incident response workflows.
- CyberSponse: An integrated security orchestration, automation, and response (SOAR) platform for efficient incident handling.
- TheHive: is an open-source incident response and case management tool designed to simplify collaboration and investigation.
8. Secure the supply chain
Protecting your supply chain from compromise is essential to ensuring the integrity of your containerized applications. The following tools aid in securing the container supply chain:
- Notary: A tool that provides trust and transparency for container image distribution and verification.
- Cosign: is an open-source tool that enables digital signing and verification of container images and artefacts.
- Harbor: An enterprise-class container registry that offers vulnerability scanning, image signing, and access control features.
- Docker Content Trust (DCT) is Docker’s built-in functionality that uses cryptographic signatures to verify the authenticity and integrity of container images.
9. Policy Enforcement
Enforcing security policies and ensuring compliance in container environments is critical. The following tools assist in policy enforcement:
- Open Policy Agent (OPA): An open-source policy engine that allows you to define and enforce policies across your container environment.
- Kyverno: A Kubernetes-native policy engine that ensures compliance and helps automate policy enforcement.
- KubeArmor is a Kubernetes security solution that provides fine-grained policy enforcement and auditing capabilities.
10. Secrets Management
Effectively managing secrets, such as passwords or API keys, is pivotal to maintaining the security of your containerized applications. The following tools aid in secret management:
- HashiCorp Vault is a popular secret management solution that offers secure storage and dynamic secret generation.
- AWS Secrets Manager is a fully managed secrets management service provided by AWS, allowing you to securely store and manage secrets.
- Google Cloud Key Management: A cloud service that enables you to manage and secure cryptographic keys and secrets.
11. Authentication and Authorization
Ensuring proper authentication and authorization mechanisms are in place is crucial for protecting container environments. The following tools enhance authentication and authorization capabilities:
- Keycloak: An open-source IAM solution that handles user authentication, authorization, and Single Sign-On (SSO) for container environments.
- Auth0 is a cloud-based IAM platform that simplifies identity management and provides robust authentication and authorization mechanisms.
- Okta is a popular cloud-based IAM platform that offers secure identity and access management services.
12. CI/CD Pipeline
Container security should be integrated into the Continuous Integration/Continuous Deployment (CI/CD) pipeline. The following tools help incorporate security practices into the CI/CD workflow:
- Jenkins is an open-source automation server that enables smooth building, testing, and deployment of containerized applications.
- GitLab CI/CD: A built-in, cloud-native CI/CD solution with strong container security capabilities.
- GitHub Actions: A flexible and scalable CI/CD platform that supports container security integrations.
Out of All the tools, trivy is the best tool that identifies the vulnerabilities.
What is Trivy?
Aqua Security developed Trivy, an open-source tool for scanning for vulnerabilities and misconfiguration problems. This tool operates on several levels: it can assess Infrastructure as Code, investigate container images, provide configuration file help, analyze Kubernetes implementations, and review code in a Git repository. Trivy’s ease of use allows it to be easily incorporated into a CI/CD pipeline (DevSecOps) by installing and adding binaries to the project. Trivy provides total visibility across programming languages and operating system packages, as well as a large vulnerability database that enables rapid scans of significant CVEs. With many new enhancements in technology, pen-testers and cybersecurity experts can now ensure continuous scans, making DevSecOps quicker and more efficient.
Targets were trivy-focused?
Trivy (pronunciation) is a comprehensive and versatile security scanner. Trivy has scanners that look for security issues and targets where it can find those issues.
1. Targets (what Trivy can scan):
- Container Image
- Filesystem
- Git Repository (remote)
- Virtual Machine Image
- Kubernetes
- AWS
2. Scanners (what Trivy can find there):
- OS packages and software dependencies in use (SBOM)
- Known vulnerabilities (CVEs)
- IaC issues and misconfigurations
- Sensitive information and secrets
- Software licenses
How do install Trivy?
The installation is quite simple. Follow the below-given commands to install Trivy from the official repository on your Ubuntu machine.
sudo apt-get install wget apt-transport-https gnupg lsb-release wget -qO https://aquasecurity.github.io/trivy-repo/deb/public.key | sudo apt-key add echo deb https://aquasecurity.github.io/trivy-repo/deb $(lsb_release -sc) main | sudo tee /etc/apt/sources.list.d/trivy.list

sudo apt-get update sudo apt-get install trivy
How do I use Trivy?
Scanning Git Repository
As I have described above, we can use trivy to scan security loopholes among multiple platforms.
If you are using the Git Repository, you can scan Git files directly without downloading the entire package.
sudo trivy repo https://github.com/<reponame>

Scanning Container Image
With the ever-growing threats to Docker security, Trivy is one of the best tools available on the market for scanning container images.
You can easily run a quick scan on the docker images to report any vulnerabilities by following the below-given steps.
Step 1: Check the Image ID of the Container image you want to scan.
sudo docker images

Step 2: Use the below-given command to scan the container image.
sudo trivy image 4621d4fe2959
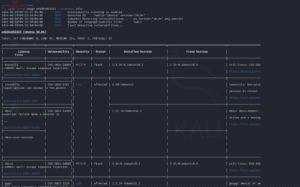
You can also scan the images for a particular severity of vulnerabilities and save the report in text format using the below-given command.
sudo trivy image --severity HIGH 4621d4fe2959 > result.txt
tail result.txt
Scanning Filesystem
Trivy can be used to scan a filesystem (such as a host machine, a virtual machine image, or an unpacked container image filesystem).
(Note: We are using a vulnerable node from Filesystem for this practical.)
Use the below-given command to scan any filesystem for vulnerabilities.
trivy conf services/
Scanning the running Containers
You can quickly scan the running container from inside. Follow the below-given steps to scan a docker file.
Step 1: Run the docker file that you want to scan.
sudo docker run -it alpine

Step 2: Add the Trivy scanner to the file and run it.
apk add curl \ && curl -sfL https://raw.githubusercontent.com/aquasecurity/trivy/main/contrib/install.sh | sh -s -- -b /usr/local/bin \ && trivy filesystem --exit-code 1 --no-progress /
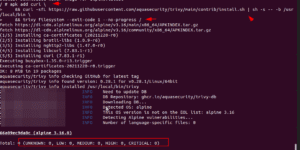
It will scan the docker file while the image is being built and report as shown below.
Conclusion:
To summarize, containers provide a lightweight, efficient, and separated environment for running programs, making them suitable for a variety of software processes. Their ability to bundle apps with all necessary components and run them flawlessly across several environments decreases development and deployment complexity. However, the increasing popularity of container-based apps raises serious security concerns. Container penetration testing is critical for identifying and mitigating vulnerabilities, guaranteeing strong security throughout a container’s lifespan. The use of both static and dynamic analysis methodologies, as well as a complete security plan and relevant tools such as Trivy, improves containerized system security. Organizations can keep their container environments secure and efficient by addressing common security concerns and incorporating security practices into the CI/CD pipeline.
Disclaimer:
This or previous programs are for educational purposes only. Do not use it without permission. The usual disclaimer applies, especially given the fact that Cyberpedia is not liable for any damages caused by direct or indirect use of the information or functionality provided by these programs. The author or any Internet provider bears no responsibility for the content or misuse of these programs or any derivatives thereof. By using these programs, you accept the fact that any damage (data loss, system crash, system compromise, etc.) caused by the use of these programs is not Cyberpedia’s responsibility at all.