The Proxy tab allows you to modify and send intercepted requests and view your request history.
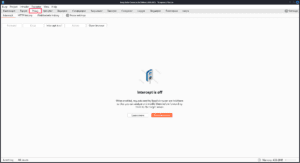
When you first view this tab you won’t have any intercepted requests and modify the request.
If you turn intercept on and make a request to the site, like reloading the page, you will see the request get caught here.
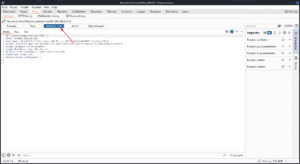
The request in the middle you can edit however you want before pressing Forward to send the request to the web server or Drop to drop the request and not send it at all. You can also click on the pencil icon above Forward to change the host that the request is sent to or select HTTP/1 in the Inspector to change the request to HTTP/1.
You can use the orange button on this page to open the BurpSuite web browser. It is a Chromium browser that is automatically set up to use BurpSuite for its traffic and it also has an extension that is very useful for DOM-based cross-site scripting attacks.
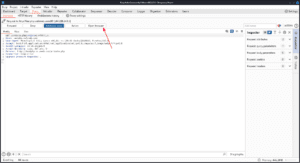
You can see the same Inspector on the right that can be used to view and modify the attributes and headers, as well as see the character length and decoding of selected text.
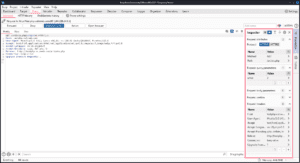
If you press the Action button or right-click on the request you intercepted, you will see you have many options for what to do with the request. I’ll give some brief summaries of each section of this menu below.
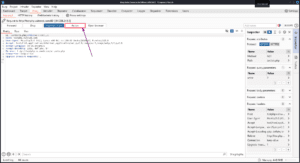
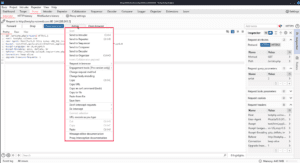
Below that, you can send the request to the other tabs in BurpSuite. Request in browser lets you send the selected request from your browser so that you can view the response there or interact with it further.
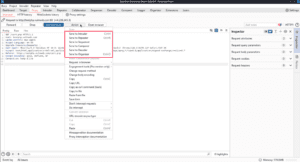
The Engagement tools option has a series of useful features:
- Find references will search all of the BurpSuite tabs for any mention of the selected host/folder/item in any responses. This can be helpful, for example, if you want to search all the responses you have for any links to a certain URL.
- Discover Content will crawl the site with a wordlist that will help to find more endpoints. This is definitely one of the more useful features of BurpSuite and will be something you want to familiarize yourself with.
- Schedule task can be used to create a task that can happen at specified times or intervals. You can create something like CRON jobs with this, or you can use it for specifically timed request chains for something like testing a complicated authentication process.
- Generate CSRF PoC can be used to generate HTML that will cause the selected request to be issued, which is helpful for CSRF attacks.
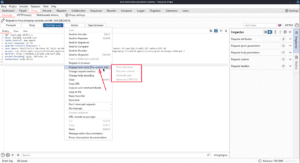
Below that, you can toggle the request method from GET to POST or switch the encoding of any message body between standard URL-encoded and multipart. Copy the URL will grab the host header and append the request target so you get an entire usable URL instead of something like /users. Copy as a curl command can be used to make the request from your terminal. Copy to file saves the request to a file, and you can paste it back to burp with Paste from file, and Save item saves the request and response as an XML object.
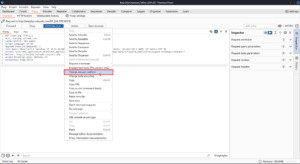
Don’t intercept requests can be used to avoid intercepting requests to this host, IP address, file extension, or directory. You can also use Do intercept to reverse that change.
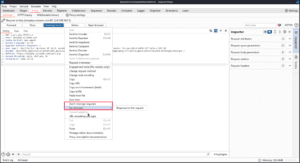
Convert selection allows you to convert selected text to URL, HTML, Base 64, or Base64 URL encodings or construct the string with JavaScript or some SQL types. You can also encode just special characters, which is useful for bypassing filters while still keeping your payload legible.
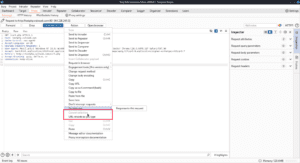
Selecting the HTTP history tab lets you look through recent requests. This uses the same filter as the Target tab which allows you to filter out of scope requests or 400 errors. The WebSockets history allows you to see the same information for WebSockets activity.
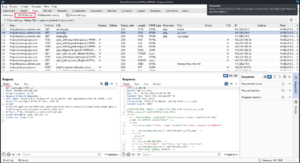
The Proxy settings allow you to customize your proxy listeners, but one especially useful feature in these settings is the interception rules. These allow you to only capture requests or responses that match these rules, with one of the most common uses being to only capture in-scope traffic.
The Burp Suite Proxy Component is an essential tool for anyone diving into web application security. It puts you in the driver’s seat, allowing you to intercept and examine web traffic, making it easier to spot vulnerabilities and understand how your target applications behave.
In our next blog, we’ll explore another important part of Burpsuit the Repeater component. This tool lets you manually tweak and resend requests, which can be a game-changer in vulnerability testing.
Stay tuned for more on that!
Thank you for reading, and as always, happy testing!



