Our world is changing at a rapid rate, thanks to the Internet of Things (IoT). These gadgets are easily becoming a part of our daily lives; examples include smart automobiles and smart heating and cooling systems. However, the security of these networked systems presents a new issue along with this comfort.
This blog post will take you through the exciting field of IoT penetration testing, also known as pen testing, which is an essential procedure for protecting the IoT ecosystem.
-
IoT Pentesting: Why Is It Important?
Consider a scenario in which a hacker gains access to your smart home temperature control, setting up the temperature during the winter and increasing the price of energy. This is but a small sample of what might happen if IoT devices are not secured. Vulnerabilities can be used by malicious actors to steal information, interfere with operations, or even carry out extensive attacks.
Before attackers can take advantage of these vulnerabilities, IoT pentesting proactively finds them. By simulating actual cyberattacks, security flaws in hardware, software, and communication protocols are revealed.
-
How is an IoT pentest explained?
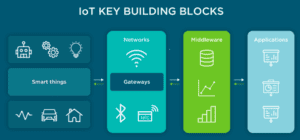
Compared to conventional pentesting, IoT device security requires a multipronged strategy. This is a quick increase in the procedure:
- Device Analysis: Examining the actual device in great detail, testers look for any hardware flaws or weaknesses that could be tampered with.
- Firmware Exploration: This process looks for vulnerabilities and misconfigurations in the firmware, the underlying software that runs the device.
- Network traffic sniffing: monitors device-to-cloud platform communication to find unencrypted data or shoddy authentication procedures.
- Mobile App Evaluation: Mobile apps that communicate with Internet of Things devices are examined for security holes such as injection vulnerabilities or unsecure data storage.
-
The Advantages of Frequent IoT Pentesting
- Enhanced Security Posture: You significantly reduce the attack surface for cyber criminals by finding and fixing vulnerabilities.
- Enhanced Device Resilience: Pentesting makes sure your systems and data are protected from a variety of cyberattacks.
- Comfort: Consistent pen testing offers insightful information about your IoT security posture, allowing you to feel secure in your networked environment.
-
Starting an IoT Pentesting Project
IoT pentesting is a broad and dynamic field. To help you get started, here are some resources:
1. Establish your basis:
- Networking Fundamentals: Understand the concepts of networking, including Bluetooth, Wi-Fi, Ethernet, and Zigbee protocols. These are essential to comprehending device communication.
- Linux Knowledge: Using many of the IoT pentesting tools requires an excellent understanding of Linux. Learn the basics of system administration, programming languages like Python, and the command line.
- Web Application Security: A lot of Internet of Things devices communicate via mobile apps or web interfaces. It would be helpful to understand common online vulnerabilities (XSS and SQL injection).
2. Look into the tools:
There is a wide range of tools available in the field of IoT pentesting. Here are some well-liked choices to get you going:
- Wireshark: With the use of this free network protocol analyzer, you may record and examine network traffic flowing between devices with the goal of spotting weak or unprotected protocols.
- Ettercap: An additional free network sniffer that goes further, allowing methods such as man-in-the-middle attacks to take advantage of communication flaws.
- Nessus Professional: Although it costs money, Nessus Professional provides an extensive collection of vulnerability scanners, some of which are especially made for Internet of Things devices.
3. Perfect Practice:
- Build a Lab: Create a regulated space for experimentation. This might involve utilising affordable Internet of Things devices like Raspberry Pi’s or easily accessible virtual machines.
- Begin with the basics: Start with simple gadgets like fitness trackers or smart light bulbs. Move to more sophisticated gadgets with network connectivity as your confidence grows.
- Follow Tutorials and Challenges: There are plenty of tutorials and challenges available online that have been created especially for those who want to become IoT pentesters.
- Become a Part of the Community: Use communities and forums to establish connections with other IoT security enthusiasts. Talk about your experiences, pick up tips from others, and keep up with the newest tools and vulnerabilities.
4. Ethical Points to Remember:
- Always seek permission. Never try a pentest on a system without getting permission to do so. The important thing is to disclose responsibly.
- Observe boundaries: avoid damaging the target system and only conduct tests within the planned scope.
- Record your conclusions: Clearly record any vulnerabilities found and offer suggestions for fixing them.
Scenario-based IOT testing:
1. Definition of Scope:
A homeowner has hired you to perform a pentest on their smart locks, security cameras, and heating and cooling systems, among other Internet of Things gadgets in their home.
The aim is to find security holes that an attacker may use to access the home’s IoT devices without authorization and risk the security and privacy of the homeowner.
2. Reconnaissance:
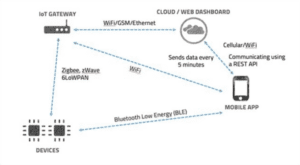
- To begin, do reconnaissance to learn more about the Internet of Things devices in the smart home.
- To find open ports and services connected to the devices, use programs like Nmap and Shodan.
- Find out that the smart home features multiple internet-connected devices, such as an August smart lock, Ring doorbell camera, and Nest thermostat.
3. Device Enumeration and Identification:
- List all of the features and interfaces that every Internet of Things device has to offer.
- Find out that the August smart lock connects via Bluetooth and has a mobile app for remote door locking and unlocking, the Ring doorbell camera has a mobile app for video surveillance, and the Nest heating and cooling system has a web interface for remote temperature management and monitoring.
4. Vulnerability Assessment:
- Scan the Internet of Things (IoT) devices in smart homes for vulnerabilities.
- Learn that the heating system manufactured by Nest is operating on out-of-date firmware that has known vulnerabilities that might let a hacker take control of the device and run arbitrary code remotely.
- Discover that the default credentials for the Ring doorbell camera have not been altered, leaving it open to unwanted access.
- Determine the month of August’s smart lock’s inadequate encryption system, which might allow an attacker to intercept and decrypt Bluetooth communications.
5. Exploitation
- Take advantage of the flaws found in the August smart lock, Ring doorbell camera, and Nest heating system.
- To obtain unauthorised access to the Nest heating system and its data, use Metasploit to take advantage of the remote code execution vulnerability in the heating system.
- Use the default login credentials to access the Ring doorbell camera and see recorded and live video feeds without requiring authentication.
- Using a software-defined radio (SDR), intercept Bluetooth connections between the August smart lock and its mobile app. Then, decrypt the communication to generate commands and open the door.
6. Post-Exploitation
- To keep access to the compromised IoT devices after the pentest is over, create resilience in them.
- Take private information out of the Nest control panel, like temperature preferences and patterns of house occupancy.
- Hack the Ring doorbell camera to turn off live video feeds and motion detection, compromising the security monitoring of the house.
- Open the August smart lock from a distance to show that the house is physically accessible.
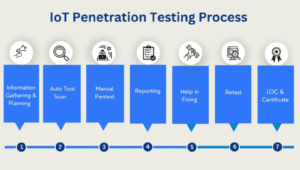
7. Reporting.
- Write a thorough report outlining the IoT pentest’s conclusions.
- Describe the vulnerabilities found, the exploitation strategies employed, and any possible effects on the security and privacy of the homeowner.
- Give specific recommendations for fixing the issue, like upgrading the firmware, altering the default login, and putting in place more robust encryption techniques.
- Highlight how crucial it is to secure Internet of Things (IoT) smart home equipment to prevent illegal access and privacy violations.
8. Remediation and Follow-Up:
- Assist the homeowner in addressing and fixing the vulnerabilities found.
- Help with adopting security best practices, firmware updates, and password changes for IoT devices in smart homes.
- To confirm that remediation activities have been successful and that the smart home’s safety condition has improved, do follow-up assessments.
- Assist the homeowner in maintaining a safe and private Internet of Things environment by providing continuous support and direction.
Conclusion:
IoT vulnerability assessment is critical for securing a world that is becoming increasingly interconnected. By proactively detecting and fixing vulnerabilities, IoT pentesting improves device security, resilience, and user confidence, protecting the integrity and privacy of our smart surroundings in an era of growing cyber-attacks.