Introduction
Capture the Flag (CTF) challenges are a popular way for cybersecurity enthusiasts to test their skills and learn new techniques. While they can be daunting for beginners, a systematic approach can make them much more manageable.
This blog post will outline a five-step methodology for cracking CTF challenges:
- Reconnaissance and Research
- Scanning and enumeration
- Exploitation
- post-exploitation and Flag submission
- Documentation
1. Reconnaissance and Research
Objective: Collect as much information as possible about the problem.
Reconnaissance is the first step in any CTF challenge, meaning understanding the challenge and gathering relevant information.
- Understanding the Challenge: Start with a close reading of the challenge description. Look for any hints or specific instructions that might suggest your methodology. Identify whether the challenge is web, binary, cryptography, or forensics-based to adapt your approach.
- Gathering Information: Use various tools and resources to gather information about the target. Use search engines like
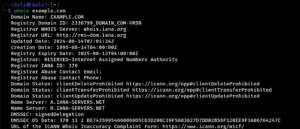
Google,Shodanto gather network information, andWHOISto gather more information about domain registrations. Look through any files or resources associated with it for hidden clues.
whois example.com
- Tech: Divide the challenge into smaller, more manageable parts. Investigate usual techniques and tools that belong to the challenge category. If the challenge belongs to a web category, familiarize yourself with general web vulnerabilities.
Example: Take web-based CTF testing as an example. To analyze the HTTP headers and response codes. Tools like Burp Suite or OWASP ZAP can be used to probe the web server to identify any vulnerabilities.
2. Scanning and Enumeration
Objective: Determine any vulnerabilities and gather overall information on the target.
Once you’ve gathered preliminary information, it’s time to delve deeper with scanning and enumeration.
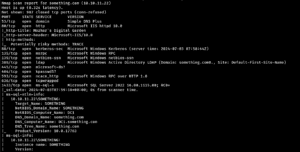
- Scanning: This can be achieved by using tools like
Nmapto recognize open ports and services for network scanning. This lets one identify the possible attack surface.
nmap -sV -sC -oN nmap <IP>
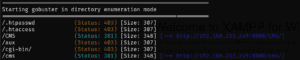
For web challenges, tools such as Nikto or gobuster can be used to find directories and files that might be vulnerable.
gobuster dir -u http://10.10.11.22 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
- Enumeration: Enumerate users, files, and other resources that could be exploited. For binaries, use tools like
stringsorGhidrato extract valuable information. - Tactic: Scan and enumeration results are analyzed in order to identify vulnerabilities. Prioritize these based on their potential impact and how exploitable they are.
- Example: Scanning the network using
Nmap, you might notice an open port 80 that represents a web server, and after this, it would be great to employNiktofor testing known web server vulnerabilities.
3. Exploitation
goal: To use the known vulnerabilities to gain access to or recover the flag.Having identified the vulnerability, exploitation follows next; that is, actively making use of it to gain access or extract the flag.Exploitation Techniques: Considering the type of challenge, use methods such as SQL injection, Cross Site Scripting, or even command injection specifically tailored toward web-type challenges.
sqlmap -u "http://example.com/vulnerable.php?id=1" --dbs
- For binary exploitation, use techniques such as buffer overflow attacks or reverse engineering.
- Tools: Automated tools such as
Metasploitcan automatically exploit known vulnerabilities. In cases of manual exploits, tools likeBurp SuiteorImmunity Debuggerare worth gold.
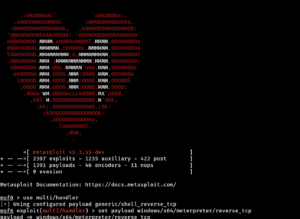
Craft or adapt exploit code based on the vulnerability you’re targeting. Test your exploits in a controlled environment to avoid unintended consequences.
In the case of a SQL injection vulnerability, one can use sqlmap to automate the process of data extraction from the database; alternatively, he might execute it himself by writing the SQL query.
4. Post-Exploitation and Flag Submission
Objective: After gaining access, escalate privileges if necessary, and capture and submit the flag.
In case of post-exploitation after the successful exploitation of vulnerability, capturing flags is of high priority.
- Post-Exploitation: If required, elevate your access level to gain greater control. Utilize tools like
LinPEASon Linux andPowerUpon Windows to elevate your privilege level on each platform, respectively. Extract sensitive information or additional flags from the exploited system.
./linpeas.sh

- Flag Submission: Ensure that you’ve correctly captured the flag and that it meets the challenge’s format. Submit the flag through the challenge’s interface or as directed.
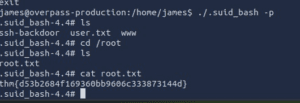
- Tactic: Verify if the format of a flag is correct according to the rules provided in the challenge. Collect any additional information or insights gained during exploitation.
5. Documentation
Objective: Record each step, findings, and lessons learned.
The last step is documenting your work. Documentation ensures that your work is organized and may be a reference in the near future.
Documentation: Document everything that happens within the methodology, including the tools used and commands executed. Where appropriate, include screenshots or logs as supporting evidence for a process.
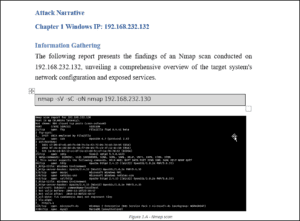
- Lessons Learned: Reflect on any challenges faced and how you overcame them. Note any improvements or alternative approaches for future challenges.
- Plan of Action: Document all findings with a clear and structured format. Share your findings in the community or refer to them as a reference for future CTFs.
Conclusion
This five-step approach can be used to address CTF challenges in an effective way. Each step progresses from preliminary research to the capture of flags and adequate documentation. You get more experienced, fine-tune your approach, and keep up with any new tools and techniques that are currently trending within the CTF community. Feel free to change this approach according to your experiences and the type of each challenge. Happy hacking!



