Intruder is incredibly useful for automating attacks. For a useful walk-through of how it works, I will use one of the PortSwigger web academy labs as a demonstration.
In this example, I have found an issue on their login page. When I provide a username that doesn’t exist the response (line 53) tells me that I provided an “Incorrect username”. That means I can try to log in with a list of usernames until I get a different response that might be something like “Incorrect password”.
To do this, I right-click on the request and select Send to Intruder.
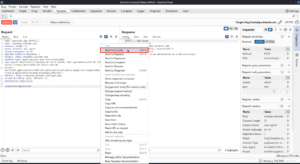
In the intruder tab, I can select the type of attack I want to use. Each has a summary of what the attack does. In my case, I want to use a single list of payloads (usernames) in one payload position (the username field), so I will use the Sniper attack.
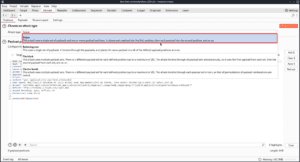
Next, you can select the payload position where you want the payload to end up. In my case I want to use the username field, so I will select whatever text is already there and click on the Add § button on the right. The “§” character is used by intruder to tell where the payload positions are, so you can also copy and paste the character and place it manually.
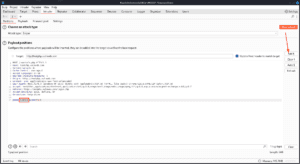
After that, we can go over to the Payloads tab to select what payloads we want to insert into the selected positions.
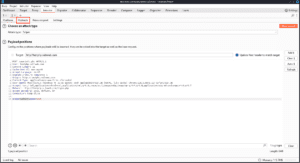
There is a huge list of payload types you can use based on what type of data you want to populate in the field you have selected for the payload position. You can have iterating numbers, wordlists, brute forcers, and character frobbers which can be used to change one character at a time in an input to see what characters affect behavior.
In my case, I want to use a wordlist of usernames, so I will go with a Simple list.
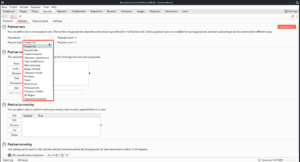
PortSwigger provides a username wordlist to use for the labs so you don’t have to spend a huge amount of time brute forcing, so I will just paste that in the Payload settings [Simple list].
In my case, I won’t need any payload processing. That said, this is definitely one of the areas where BurpSuite shines. You can add complex logic here about how to process the payload which can allow you to carry out very involved attacks.
One good example of this is attacks on JSON web tokens. Say you have a username stored in a JWT that is not properly signed. You can brute force the username with a simple wordlist, but then with each username you can add the rest of the JWT as a prefix and suffix and then Base64 encode the entire JWT before adding it into the request.
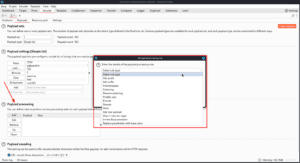
Next, we can use the Resource pool tab to set how many concurrent requests we want to send, as well as add delays between requests or throttling when we start to see certain error messages. In my case, I will bring my resource pool down to a single concurrent request to avoid errors, since my wordlist is small.
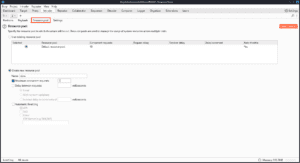
The Settings tab allows us to add even more complex logic to our attack. For my attack I will use the Grep — Extract section of the settings to open up the original response I got and select the “Invalid username” we were seeing before.
By clicking the Extract the following items from responses: checkbox, this string will be read from the responses in the table of results after we run the attack, and then I can just sort by rows of the table that don’t include this string to find the valid usernames.
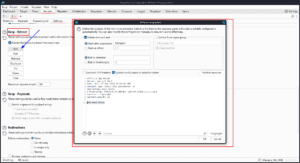
The Settings tab also allows you to do the following:
- Retry failed connections
- Flag found strings in the response with Grep-Match (This works like Grep-extract but instead of adding the found string to the table, it adds a 0 or 1 to the table if it is found or missing)
- Flag results that include the used payload. You can use this to search for reflected XSS with a wordlist of payloads
- Follow redirections
If we click on the Start attack button when we are done with the settings, we will see the results window pop up. As you can see the Grep — Extract is pulling the “Invalid username” from the response into another column. If I sort that column you can see that one username had a different response because the username is valid.
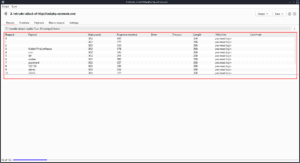
If I go back to the payload in intruder and put admin in the username field and set the password field as the payload position, I can add the provided password wordlist as the payload and run the attack again.
As you can see, the admin password did not give us the “Incorrect password” error, so we can try to log in with test:test and we successfully log in and solve the lab.
The Burp Suite Intruder Component stands out as a powerful tool for automating attacks and customizing your testing efforts. Whether you’re brute-forcing login credentials, fuzzing inputs, or probing for vulnerabilities, Intruder gives you the flexibility and control needed to launch targeted, efficient attacks.
In the next blog, we’ll dive into the Decoder Component, a tool that helps you quickly decode or encode data formats, making it easier to handle encrypted or encoded information during your security assessments. Stay tuned as we explore how Decoder can streamline your workflow.
Thanks for reading, and happy testing!



