What is CAPTCHA?
Web applications use the CAPTCHA security measure to stop automated bots from accessing their resources. CAPTCHA stands for Completely Automated Public Turing Test to Tell Computers and Humans Apart. CAPTCHA mechanisms typically involve presenting the user with a challenge that requires human intelligence to solve, such as identifying distorted text, choosing specific images, or solving mathematical equations.
Types of CAPTCHA:
-
Text-based CAPTCHAs
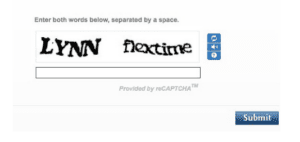
-
CAPTCHA Image

-
Audio CAPTCHA
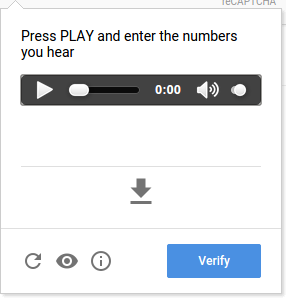
-
Math or Word Problems
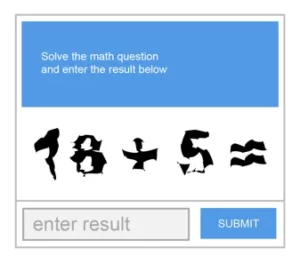
-
No CAPTCHA ReCAPTCHA

What are CAPTCHAs used for?
Any website that wants to prevent bot usage uses CAPTCHAs. Specific uses include:
-
Preserving the integrity of the poll:
By verifying that each vote is submitted by a human, CAPTCHAs help stop poll manipulation. Although this does not limit the overall number of votes that can be cast, it makes the time required for each vote longer, discouraging multiple votes.
-
Limiting registration for services:
Services can use CAPTCHAs to prevent bots from spamming registration systems to create fake accounts. Restricting account creation prevents waste of a service’s resources and reduces opportunities for fraud.
-
Prevent ticket inflation:
Ticketing systems can use CAPTCHA to limit scalpers from purchasing large numbers of tickets for resale. It can also be used to prevent false registrations for free events.
-
Preventing false comments:
CAPTCHAs can prevent bots from spamming message boards, contact forms, or review sites. The extra step required by a CAPTCHA can also play a role in reducing online harassment through inconvenience.
Why use HTTP-Trace-enabled login scanners?
HTTP-Trace-enabled login scanners can detect security flaws in web applications by obtaining the entire request message sent to the server. These scanners can extract the CAPTCHA challenge presented during the login process and solve it using OCR or other image recognition techniques, bypassing the CAPTCHA mechanism and gaining unauthorized access to the application.
How do I use HTTP-Trace-enabled login scanners in the Metasploit Framework?
Although login scanners are included in the Metasploit Framework, they are not by default compatible with HTTP-Trace enabled login scanners. However, problems and vulnerabilities in login pages for online applications can be discovered by employing HTTP-Trace enabled login scanners. Attackers frequently utilize password-guessing attacks to obtain sensitive data, and the framework’s fundamental features enable the execution of these kinds of attacks. Conventional password guessing techniques are slow and frequently ineffective against anti-brute-force systems. However, login scanners with HTTP-Trace enabled can get around these defenses by sending an HTTP-Trace request to the server and analyzing the response. The user credentials will be included in the response that the scanner receives if the web application is vulnerable.
Methodology:
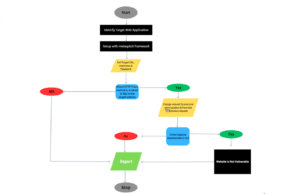
- Choose the intended web application: Select the web application to be tested and ensure you have the necessary permission and authorization to run the test.
- Setup with the Metasploit Framework: To perform HTTP-Trace-enabled login scans, configure the Metasploit Framework with the necessary plugins and modules, such as the HTTP-trace module.
- Gather information: Gather information about the target web application, such as the URL of the login page, form parameters, and other relevant information.
- Carry out authentication attacks: To carry out authentication attacks against the target web application, use the HTTP-Trace-enabled login scanner to send a variety of requests to the login page with varying usernames and passwords.
- Observe the results: Look into the outcomes of the authentication attacks to see if any authoritative credentials have been discovered, and then use this knowledge to gain access to the system being targeted.
- The following are the report’s findings: Each and every vulnerability or weakness discovered during the test should always be reported to the appropriate parties, such as the software engineer, system administrator, or security officer.
- Mitigate vulnerabilities: Collaborate with both the application’s developer and system administrator to address any flaws or weaknesses discovered during the test, and make sure that the appropriate security measures are in place to prevent similar attacks in the future.
- This code creates a brand-new auxiliary module that searches for HTTP servers that accept the TRACE method and makes login attempts using a list of supplied credentials. To send a TRACE request using the supplied credentials, it makes use of the send request cgi method from the Msf::Exploit::Remote::HttpClient mixin. The login attempt is deemed successful if the server replies with a 200-status code and the word TRACE in the response body. Otherwise, it views that as a failure.
- It’s necessary to keep in mind that this method is only one way to improve the Metasploit Framework’s functionality by using HTTP-Trace-enabled login scanners. It may need to be customised or modified depending on the target application and test objectives. Furthermore, it is critical to follow accepted best practices for penetration testing and responsible disclosure, as well as to ensure that all testing is done with the appropriate permission.
POC:
1. First, create code and save it in the Metasploit Framework module. Path: /usr/share/metasploit-framework/modules/
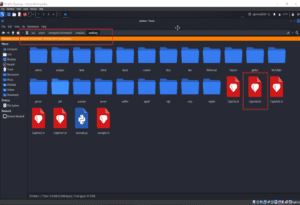
Figure 01: Save code in metasploit framework
2. Then reload the module of the Metasploit framework to add my created code to the framework.
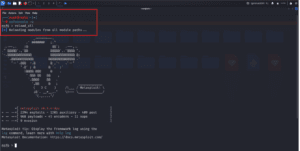
Figure 02: Launch and reload metasploit framework
3. Then search for the added module using the command search captcha.
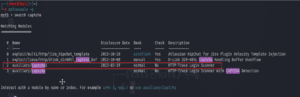
Figure 03: Search the module
4. Now check what the requirements are to check the website vulnerabilities.
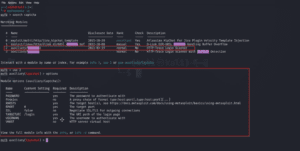
Figure 04: Select the module and check the requirements
5. Now set all the values, like URL, rhost, rport, username, and password.
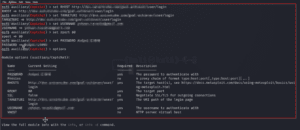
Figure 05: Set the requirements
6. Now run the module.
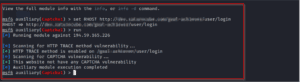
Figure 06: Final output
Conclusion:
- The usage of CAPTCHA platforms to prevent automated attacks on online applications is growing, despite the fact that research has demonstrated that many CAPTCHA techniques can be bypassed using automated tools like the Metasploit Platform with HTTP-Trace-enabled login scanners.
- According to the study’s research, web applications that employ CAPTCHA techniques are vulnerable to attack. Metasploit Framework and login scanners that support HTTP-Trace might be useful in this situation.
- Several studies have suggested creative methods for getting over CAPTCHA protections utilising image processing, machine learning, and deep learning methods. Other studies have demonstrated that it is a prudent practice to assess the efficiency of CAPTCHA defences against automated assaults on web applications using the Metasploit Framework and HTTP-Trace-enabled login scanners.



